Cybersecurity Perceptions Study 2023 Results
Over the past few years, I’ve had the good fortune to work with fantastic people from the University of Massachusetts Dartmouth. One of those is Dr. Timothy Shea. Tim has recently retired, and as one of his last research projects, he asked me if we could update the work we did in 2020 regarding Cybersecurity Governance and Oversight by Management Teams.
In that study, we found that there was still a lot of work that management teams needed to do to improve their oversight and governance of all things cyber. That study was conducted during the dark days of the pandemic, and there were so many concerns about the rapid move to work from home and other seismic shifts in how companies operate that there was a lot of uncertainty and unknowns about the cyber risks they faced.
Management is Serious About Cyber
This time, we are in a changing economic climate with new global political challenges. Despite these external factors, we were surprised by the study results. For the most part, organizations are doing a reasonable job of planning for, identifying, and mitigating cyber risk while continuing to invest in cyber meaningfully across their enterprises.
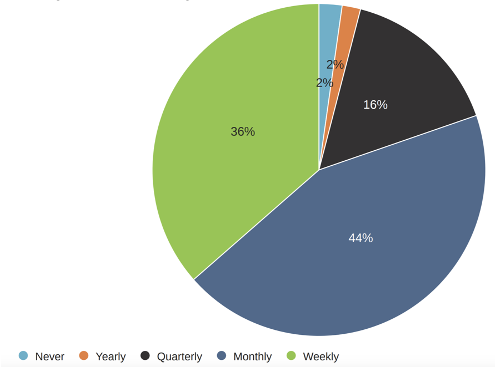
Specifically, we asked how often cyber comes up in management team discussions and how frequently cyber is discussed during strategic initiatives. The results of both questions were highly positive. Most organizations discuss cyber weekly (44%) or monthly (36%) during management team meetings. As for the strategic discussions, most organizations state that cyber is discussed when a new initiative is introduced. These factors indicate that organizations recognize the importance of cyber in their day-to-day operations and strategic thinking.
management team meetings. As for the strategic discussions, most organizations state that cyber is discussed when a new initiative is introduced. These factors indicate that organizations recognize the importance of cyber in their day-to-day operations and strategic thinking.
Another striking difference this time is how often management teams discuss cyber issues regarding strategic initiatives. More than three-quarters of those surveyed say their organizations factor cybersecurity always or most of the time for their new strategic initiatives. This fact shows that management teams are integrating cyber thoughtfully into their initiatives. Again, this contrasts the past when companies considered cyber as an afterthought. We sometimes refer to this as the “bake-in” vs. “bolt-on” approach.
Another difference that caught our attention in the data was how management teams characterize their cyber security plans or strategies. Again, more than three-quarters of the respondents described their plans as formal or very formal, while less than twenty percent characterized them as informal or non-existent. This characterization points to diligent management teams spending time and energy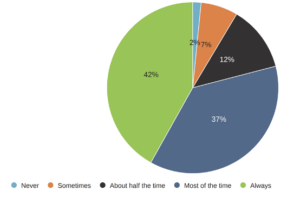 planning for cyber events more thoughtfully and proactively than a reactive approach just a few years ago.
planning for cyber events more thoughtfully and proactively than a reactive approach just a few years ago.
The last interesting point about management teams was who led the charge during a cyber incident. For the organizations surveyed, about half of the time, it was the CEO and split just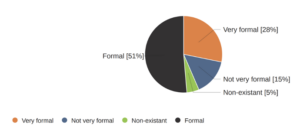 about evenly between the CIO, CISO, and the CFO. This leadership points to the fact that cyber is not a technology issue but a business issue.
about evenly between the CIO, CISO, and the CFO. This leadership points to the fact that cyber is not a technology issue but a business issue.
Management is moving forward – the troops will follow.
Ironically, all this positive movement is at the management team level of companies. Still, our friends at the Information Systems Security Association (ISSA) tell a slightly different story about their members who are cyber security professionals. They do a yearly study of their membership.
They say only 43% of their respondents have an “average” cybersecurity culture. While there is room for interpretation in the phrase, for ESG/ISSA, it means “Cybersecurity is considered a shared responsibility by some employees and is included in some business/mission initiatives.” The key is shared responsibility. “This demonstrates that although leadership has seen positive moments, there is still a disconnect between the rank and file,” says Candy Alexander, ISSA International President.
My colleague Dr. Shea points out there may be a delay in what management teams are doing and saying to the troops executing the orders.
There are some other interesting data points and correlations from our study. When asked about cyber assessments, many (78%) said they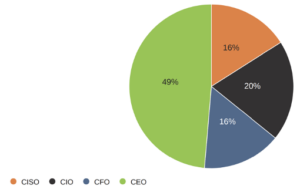 had assessed in the past two years. However, this may be because all respondents have definitely or likely experienced a breach or other serious cyber security event in the past two years.
had assessed in the past two years. However, this may be because all respondents have definitely or likely experienced a breach or other serious cyber security event in the past two years.
While most organizations were positively surprised by the results of their cyber assessments, almost three-quarters of them have made significant changes due to the assessment. Some of these changes could also be in personnel. ISSA has pointed out in their last few surveys that there is a dearth of available talent in the marketplace to fill all the cyber-related jobs.
Of the organizations we surveyed, most (89%) had a full-time CISO or equivalent role and a dedicated cyber risk or security team in the company. This shift is positive news since less than half had invested in the top cyber job the last time we did our survey. When we asked about what they would invest more in if they could, for many respondents, the best categories revolved around people, from training their staff to adding consultants or outsourcing the cyber responsibility as well as tools and technology to help their teams. According to the ISSA study, there is a significant shortage of qualified cyber professionals, and the majority of respondents to that study want to see better compensation and incentives. “Although some may report security culture as being positive,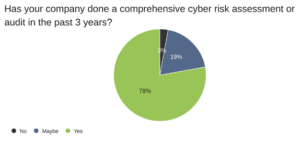 with responses of 43% being average and 31% being advanced, yet, the study suggests organizations don’t have enough or adequate skilled resources, suggesting a need for further investment in staffing to go beyond basic practices,” says Candy Alexander.
with responses of 43% being average and 31% being advanced, yet, the study suggests organizations don’t have enough or adequate skilled resources, suggesting a need for further investment in staffing to go beyond basic practices,” says Candy Alexander.
Much of this positive news on cyber is likely due to high-profile breaches, which lead to public scrutiny and backlash, but some of it has to do with the fact that government regulators are starting to pay more attention to cyber as a whole. The SEC recently finalized its rules on cybersecurity incident disclosure for public companies. Their ruling requires companies to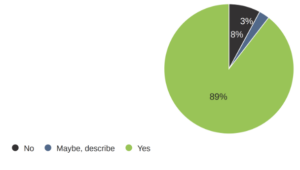 disclose within four days of an incident. While there are some breaks for smaller companies, the bottom line is that all public companies must comply by the end of 2024, regardless of size. We firmly believe this will trickle down to privately held companies as well, especially for companies that hold confidential information about their employees and customers.
disclose within four days of an incident. While there are some breaks for smaller companies, the bottom line is that all public companies must comply by the end of 2024, regardless of size. We firmly believe this will trickle down to privately held companies as well, especially for companies that hold confidential information about their employees and customers.
The takeaway from this research is that management teams are finally starting to treat cyber as the priority it should be and dedicate the mindshare and resources to address the ongoing threat adequately.
NeuEon, the Charlton College of Business at the University of Massachusetts Dartmouth, and Dr. Timothy Shea funded this study.